
Pushing the Boundaries: The Hybrid Cloud and Wireless ECM
The tension between keeping data “behind the firewall” and making it externally available is particularly acute in the context of ECM. Recently popular “hybrid cloud” solutions describe a deployment strategy in which an organization uses both on-premises architecture and cloud-based components (either dedicated or third-party hosted).
This combination architecture gives users the flexibility to share documents, internally and externally, in limited circumstances; to keep confidential, sensitive, proprietary, trade secret and/or personally identifiable information (PII) secure and perpetually on-premises; and to introduce a ready-made disaster-recovery or business-continuity component to the organization.
Among our advanced solution providers, iManage and OpenText, two of the largest ECM solution providers, have recently introduced hybrid-cloud products. Zia Consulting, an Alfresco-based solution provider, is a particularly strong hybrid-deployment enthusiast. And in a reverse application of the same concept, NetDocuments, a Cloud-based application, offers its clients an on-premises backup replication service, synchronizing copies of all documents stored in the system to client-provided on-premises hardware.
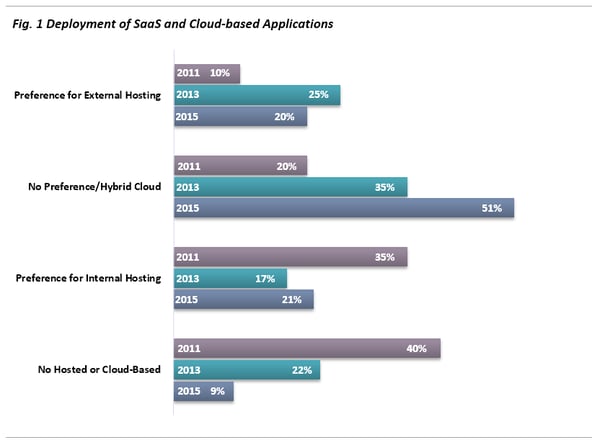
The introduction and rising popularity of the “hybrid cloud” model makes logical sense. The resistance by legal organizations to Software-as-a-Service (SaaS) Cloud deployments is indeed slowly dissipating (Fig. 1). Cloud represents the modern-day manifestation of corporate WAN-infrastructures, though predicated on the leverage of the Internet and third-party infrastructures built for global scale. Proprietary enterprises could never approximate such horsepower.
These factors, as well as the burgeoning availability of Web-based integration and support services, help make extending content boundaries an attractive and cost effective proposition. The embrace of the Cloud, however, is tempered by concerns for the security of data and regulations surrounding the residency and flow of data in a global environment where political borders increasingly compete with technological ones.
In some cases, the decision to keep data on-premises is driven by client discomfort. Much like the patient that struggles with the decision to be first to undergo a new procedure, few clients want to be guinea pigs for untested paradigms with potentially large risk exposure. Further, the availability and varying degrees of Cloud-readiness of third-party system integrations, and the need to maintain the integrity of those integrations in step, should also raise caution.
The embrace of the Cloud, generally and in legal, has been deliberate though gradual.
We see the growth of “hybrid cloud” to be a transformative influence in the adoption of cloud-based technologies and, notably, the migration of data to the Cloud. It helps to create and foster a technology infrastructure that seamlessly avails of the access and scale of Cloud while mitigating risk and concerns over control and compliance.
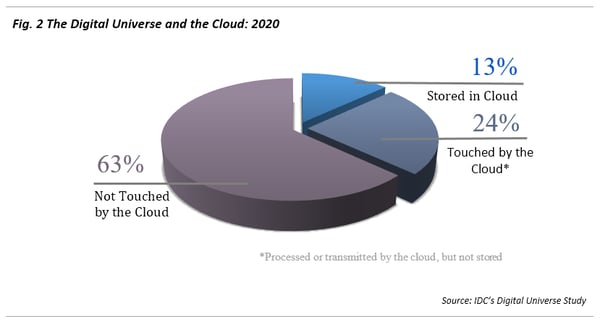
Though we expect Cloud penetration to grow, we also see it growing slowly and don’t expect it to overtake on-premises enterprises anytime in the near future. In fact, recent IDC projections predict the amount of total data “touched by the cloud” to be less than 40 percent of enterprise content by the year 2020 (Fig. 2).
Secure ECM for a Mobile Workforce
As with the Cloud, the appeal and embrace of access to ECM systems via portable wireless devices such as smartphones and tablets also continues to increase, both in the context of access on company-provided devices and with personal devices (so-called BYOD). All Advanced ECM solution providers offer an ability to access their systems via the wireless Web, whether through a browser interface or an app. While iOS is a predominantly available format, some solution providers also support Android, Windows Mobile and Blackberry. Some of the extensions of functionality to wireless being introduced are also unique and innovative. HP, for instance, which has consolidated their information management business units, has built an integrated solution that allows users to route automated forms to office printers – another key HP competency – directly from the wireless device.
With this wireless extensibility, though, come the inevitable concerns over control and security. How can administrators enforce organizational content policy? Are users commingling business data with personal data – and is that inherently a problem? What would happen if the user’s device is lost or stolen? Such concerns trouble 80 percent of organizations, who cite security as a major challenge to offering their users wireless accessibility.
These security concerns are now driving the development of new technologies that aim to “containerize” or “wrap” the ECM system environment on the wireless device. Companies like Good Technology and VMWare have introduced “mobile device management” (MDM) software. This software empowers IT administrators to set permissions and access controls dictating what a user can and cannot do on the device; to set passwords, encryption keys or other authentication requirements; to physically limit where on the device documents can live and remain; and to wipe the wireless device if it is lost or stolen.
Seeing the value of MDM as a means of driving wireless adoption, OpenText, an Advanced Solution provider covered in this report, has developed an “application-wrapping” function for its eDOCS DM for Wireless product that allows users to integrate the wireless DM with any of these MDM software options. Perhaps telling, Box, a cloud-based document repository provider with a clear and deliberate vision for legal market penetration, purchased the MDM startup Airpost in 2015.
Additional Information
For additional information about this Insight or Hyperion Research and our Market Intelligence Programs, please complete the short form below:


