
Is There Safety in Mobile?
The challenges of securing mobile while supporting the anytime, anywhere workforce
Mobility in the workplace is no longer just a concept or a talking point. For legal professionals, the use of smartphones and tablets have become ingrained into our way of working. Whether traveling, accessing information quickly when away from the desk or just checking in on the status of matters after-hours, for many of us, the use of handheld devices for professional purposes is not simply routine but required.
Yet as the prevalence of mobility technology grows, so does the need to secure the ever-expanding corporate information being used and accessed on those devices. As the recent kerfuffle over Hillary Clinton’s e-mail habits demonstrates, confidential and sensitive information can barely avoid making its way onto a BlackBerry (or an iPhone, or an Android, etc.). The path of that information—and the behavior of the device’s user--can have deep organizational consequences, especially if policy is not aligned.
With this in mind, we recently polled the Hyperion Research community about their most important priorities for implementing a mobile security policy.
The results of our poll demonstrate an acknowledgment from legal organizations that mobile is in fact an environment to be secured diligently, the same way a desktop computer, network or or Microsoft Outlook need to be secured (see Fig. 1 below).
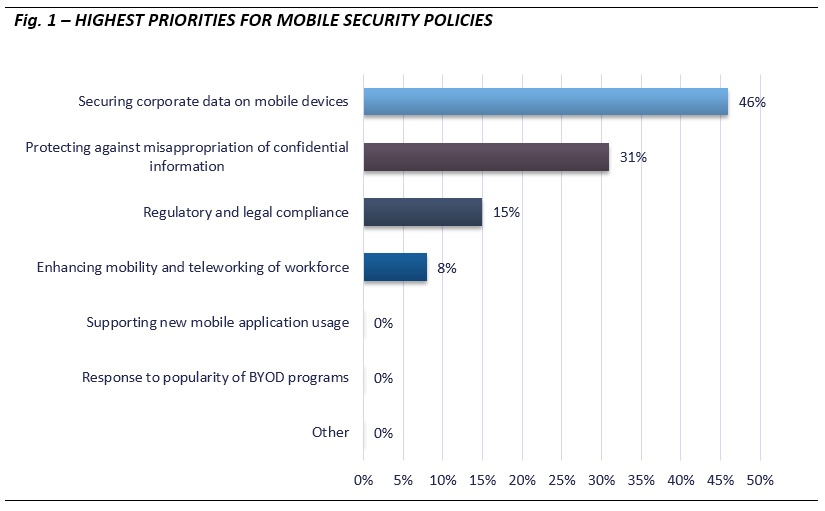
Nearly half of our respondents (46 percent) say their highest priority for mobile device management lies extending the corporate security blanket to the mobile that carry the organization’s data. The use of secure VPN environments, and the use of mobile device management (MDM) platforms are among the leading methods legal organizations use to guard against confidential and proprietary data leakage or the misuse of systems. MDM platforms give organizations particular power to control data access where confidentiality and a “need to know” basis of knowledge are crucial. The MDM tools also allow administrators to remotely wipe data in the case a device is lost or stolen, or in the case an employee leaves the organization. We expect the use of this type of administrative control of mobile devices to increase significantly over the next few years.
Nearly a third or our respondents (31 percent) listed protecting against the misappropriation of confidential information as their most important priority. Our respondents confirm a concern we’ve long observed: merely creating a safe and productive mobile working environment does not itself guarantee the integrity of confidential, proprietary or sensitive information. Breaches of confidentiality or the misappropriation of proprietary information can be innocuous in nature, including forgivable errors or errors in judgment, such as a wayward text message or e-mail. Of course, we’re all trying to be keenly attuned to the nefarious, such as the theft of invaluable trade secrets, by an organized threat or even an internal user, by a “spear-phishing” e-mail scam that targets unsuspecting executives, or even by directly stealing or hacking a device.
These threats signal that it is imperative for organizations to both develop thorough policies and procedures for mobile use and educate staff members about the stakes. Awareness of the issues is among the most important and effective means of data security. Do your employees know they’re working on matters involving trade secrets? Have you published clear and direct guidelines for how to handle such information? Also, what device settings and tools are acceptable to comply with procedure? This type of information governance and policy work is ongoing in legal, but with people and information more mobile now than ever before, now is a critical time address mobile policies, procedures, technologies and approaches.
One other aspect of the poll piqued our curiosity: The zero response rate to concerns governing the Bring Your Own Device (BYOD) programs. Given the intermingling of company devices and data with personal devices, we wonder: have we reached a point where we accept BYOD as the de facto standard, and have accepted it as the “new normal?” We’ve seen the consumerization of IT take a fundamental root hold on how users expect to work with and interact with technology. The movement has driven the vast and rapid proliferation of mobile devices by developing applications aimed at improving employee productivity and customer satisfaction. Do our concerns about content security and the policies and procedures governing the protection of corporate data simply assume BYOD as a matter of course?


