Enterprise Content Management; Advancing Toward an Integrated Ecosystem
In the first two installments in this series, we provided an overview of the current state of Enterprise Content Management (ECM) and provided some advice on how to overcome obstacles to adoption through attention to user-centric solutions features. Now we turn to attributes of successful enterprise-wide ECM systems.
With remote work becoming ubiquitous and persistent, investment in resources to secure, integrate and make content highly accessible will pay off.
Making Content Shareable: Security and the Hybrid Cloud
Thanks to clear, demonstrable investments in security, quick deployment capabilities and increasing affordability, the Cloud has become progressively more ubiquitous. Driven by high demand, advanced solution providers now offer cloud deployment as a standard feature. Even organizations we spoke to that were previously hesitant to move from on-premises solutions to the Cloud due to concerns about cost, time, or security have increasingly made the switch.
The tension between keeping data secure “behind the firewall” and making it available and shareable is particularly acute in the context of ECM. “Hybrid Cloud” solutions describe a deployment strategy in which an organization uses both on-premises and cloud-based components (either dedicated or third-party hosted). This architecture gives users the flexibility:
- To share documents, internally and externally, in limited circumstances.
- To keep confidential, sensitive, proprietary, trade secret and/or personally identifiable information (PII) secure and perpetually on-premises.
- To introduce a ready-made disaster recovery or business continuity component to the organization.
We see the growth of “Hybrid Cloud” to be a transformative influence in the adoption of cloud-based technologies and, notably, the migration of data to the Cloud, particularly for those leaving an existing on-premises server structure. It helps to create and foster a technology infrastructure that seamlessly avails of the access and scale of Cloud while mitigating risk and concerns over control and compliance which is of upmost priority in ECM.
Integrating to Connect the Dots
As legal technologists continue their efforts to build unified legal technology infrastructures, we recommend integrations to third-party productivity and practice-management systems. These integrations go further than plug-ins and add-ons to Microsoft Outlook and the Microsoft Office suite. The goal should be to enable drag-and-drop or profiling content to the DMS through Outlook, Word and the other Office programs.
Integrating systems fosters a seamless, more automated enterprise-wide configuration that connects the major functions of the law department—including matter management, intellectual property management, accounts payable and the like—with the content management system at the core. Some suggestions:
- Look for ECM solution providers that partner with other legal and enterprise technology vendors to offer tight integrations for smooth data and process flow.
- Take advantage of innovative platform solutions, such as open-source development platforms, REST APIs and the game-changing Content Management Interoperability Services (CMIS) to provide easily accessible, powerful, workflow-driven content infrastructures that are highly customizable to address your specific needs.
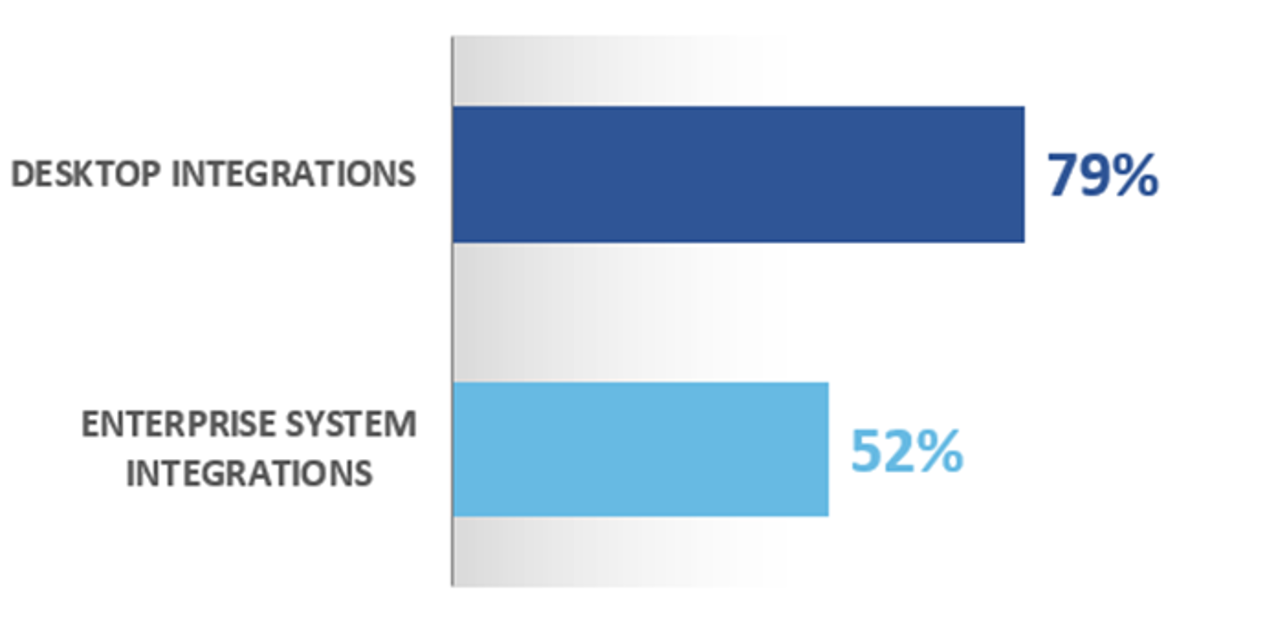
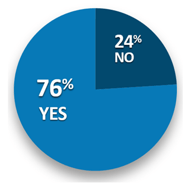
As the Hyperion Research data below demonstrates, integrations have become the norm and are deemed effective.
|
ECM Integration with Other Enterprise Software Tools
|
Reported Effectiveness with ECM Integration: Are Your Integrations Effective?
|
Leveraging Mobile ECM with Confidence
All Advanced ECM solution providers offer mobility, whether through a browser interface or an app. As an added layer of accessibility, most mobile applications offer identical functionality that mirrors desktop configurations to better suit users who often work on-the-go, including full search functionality.
Predictably, mobile access brings with it the inevitable concerns over control and security. How can administrators enforce organizational content policy? Are users commingling business data with personal data—and is that inherently a problem? What would happen if the user’s device is lost or stolen? Such concerns trouble 80 percent of organizations, who cite security as a significant challenge to offering their users mobile access.
Thanks to technologies that “containerize” or “wrap” the ECM system environment on a mobile device, as well as rapid developments in encryption and multi-factor authentication measures for both mobile and desktop configurations, mobile access has rapidly become a staple of ECM. Leading solutions providers have made significant strides in mobile security functionality, and according to our research, top concerns about mobility today revolve more around the security of back-end servers and whether or not to adopt the often-frustrating practice of using VPN access for remote staff.
With remote work becoming ubiquitous and persistent, investment in resources to secure, integrate and make content highly accessible will pay off. Admittedly, it’s not a plug-and-play situation, but rather a long-term programmatic challenge that requires putting building blocks in place with a relentless focus on how information is shared, so that you can pave the “desire paths” – making it easier to share information, repurpose work product and collaborate to deliver legal services efficiently, effectively and securely.
Hyperion Research will be conducting another deep study and analysis of quickly evolving ECM practices and solutions later this year. To be included in the benchmarking study and receive notice of the next ECM MarketView report, provide your contact information here.